Compliance that moves as fast as you do.
Automate your SOC 2, ISO 27001, and NIST RMF audits. We partner with security-forward teams to build scalable, evidence-based compliance programs.
Automate your SOC 2, ISO 27001, and NIST RMF audits. We partner with security-forward teams to build scalable, evidence-based compliance programs.

From policy generation to automated gap analysis, we've built the tools compliance officers actually want.
Generate audit-ready policies in seconds using our LLM-powered engine tailored to your industry.
Define a control once and map it to ISO 27001, SOC 2, HIPAA, and GDPR automatically.
Assign evidence tasks to team members with due dates, reminders, and review workflows.
Integrated risk register and heat maps to identify, assess, and treat security risks.
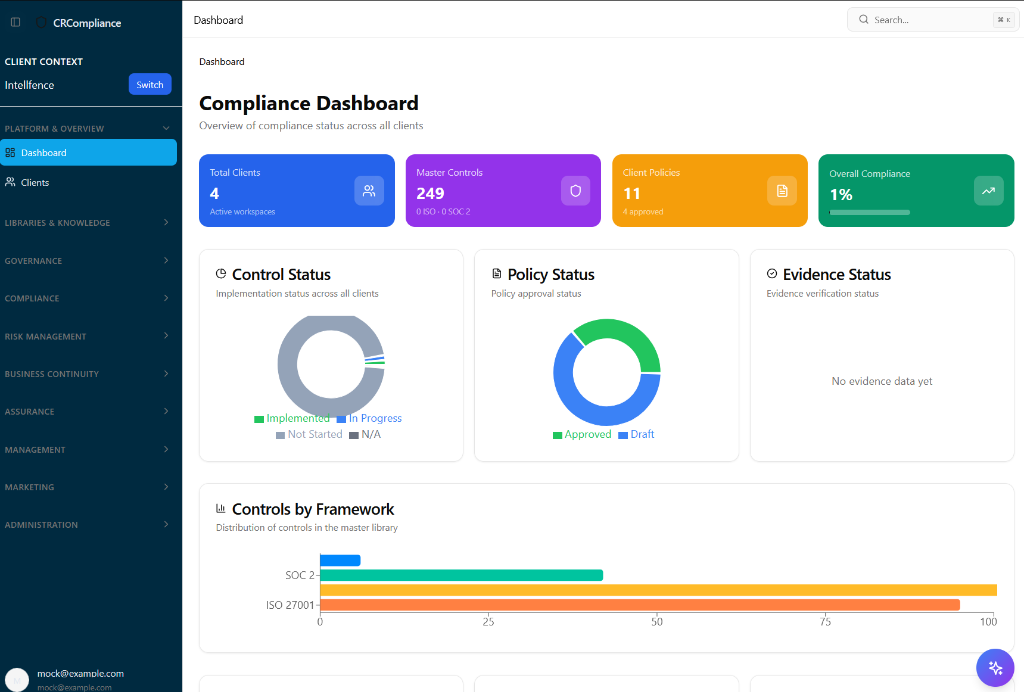
Real-time dashboards show your exact readiness score for each framework.
Track third-party vendors and their security posture in a centralized registry.
Everything you need to build, scale, and automate your security program in one unified platform.
Don't just list risks—solve them. Our guided workflows help you identify assets, assess threats, and implement treatments without needing a PhD in cybersecurity.
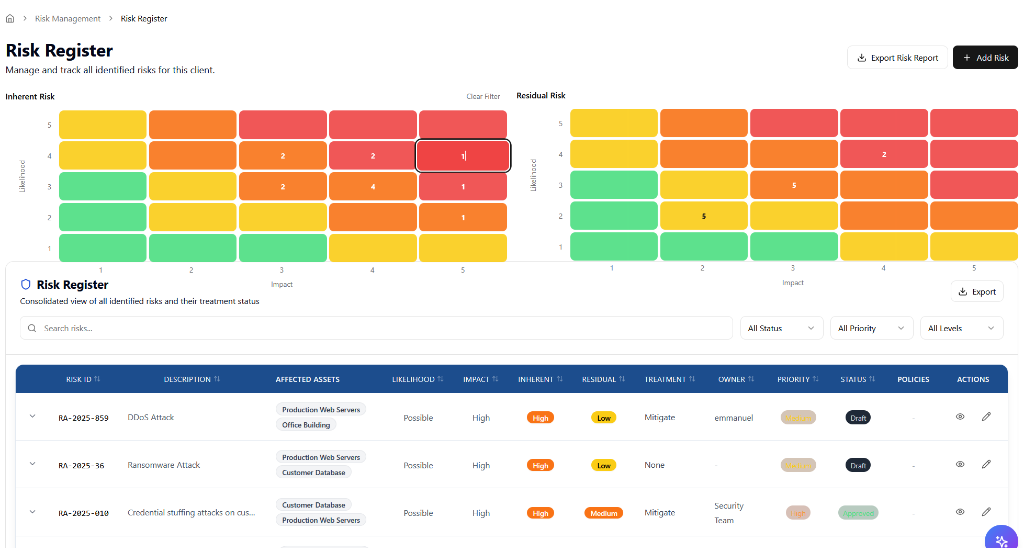
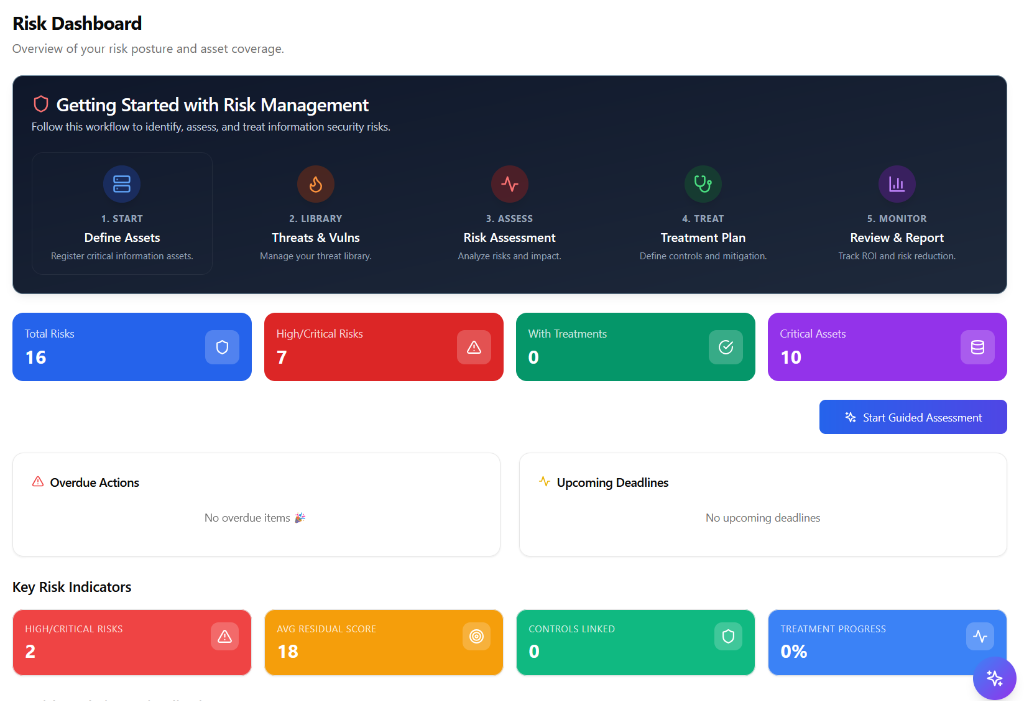
Instant heatmaps show you exactly where to focus. Filter by likelihood, impact, or asset criticality to prioritize your limited resources effectively.
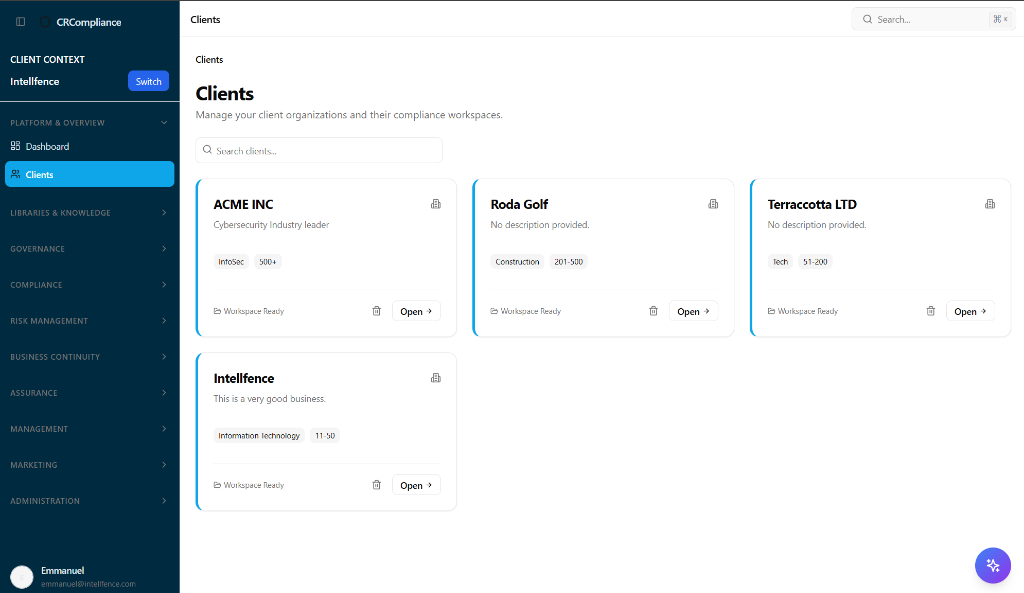
Perfect for MSPs and Fractional CISOs. Switch between client environments instantly, keeping policies, evidence, and risks completely segregated.
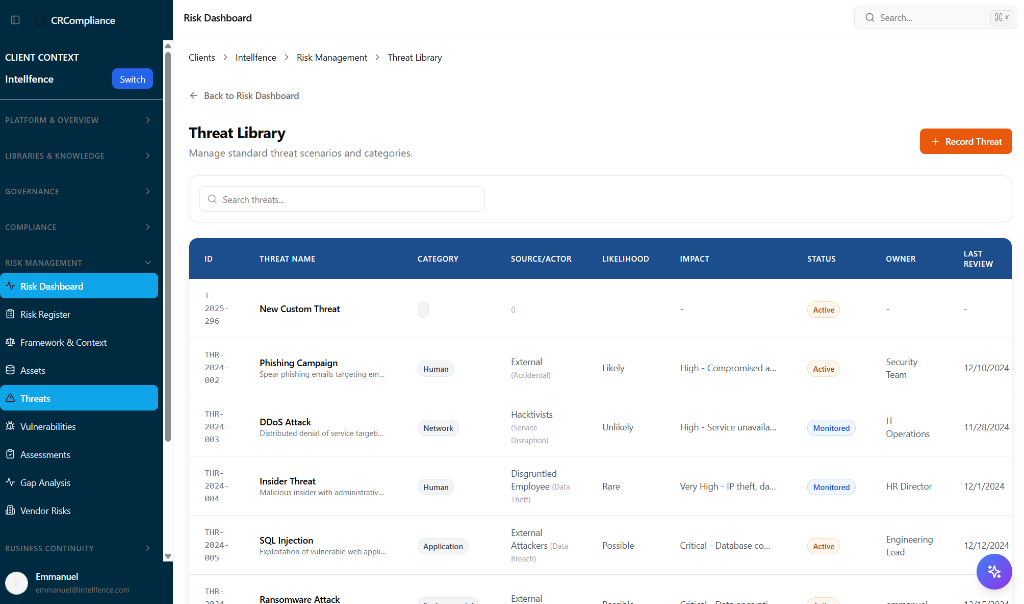
Maintain a living library of threats relevant to your industry. Map them to vulnerabilities and assets to understand your true exposure.
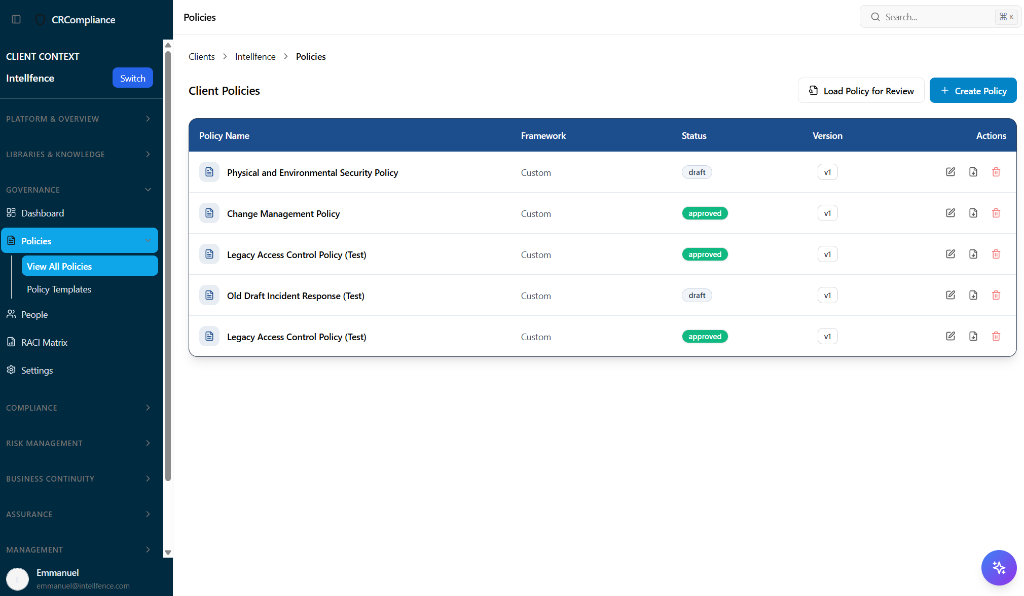
Stop chasing Word docs. Manage the entire policy lifecycle—from drafting and approval to version control and employee acknowledgement—in one place.
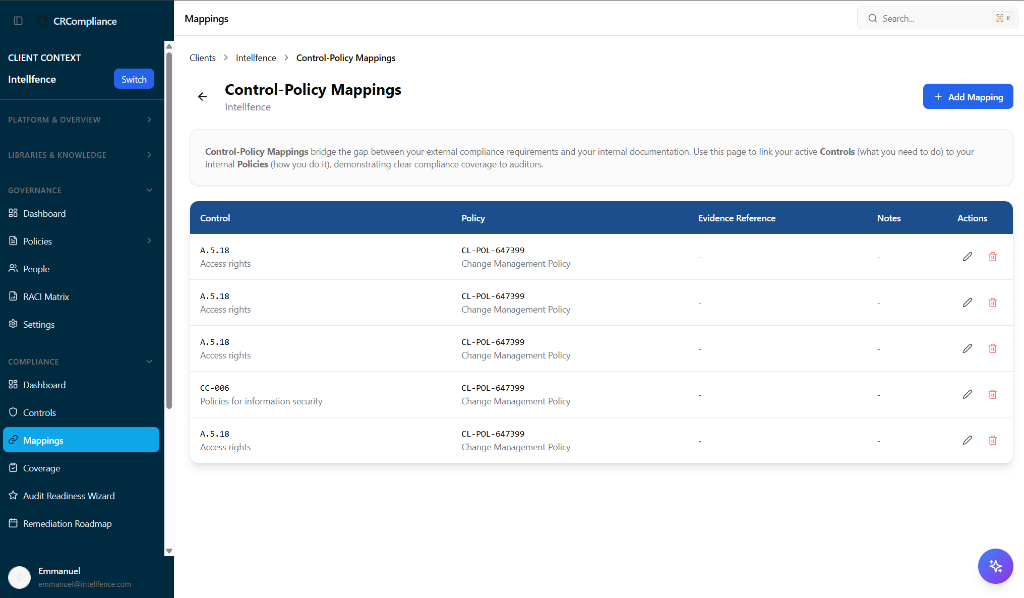
Link your internal controls to policies and evidence. Our smart mapping engine visualizes coverage gaps instantly.
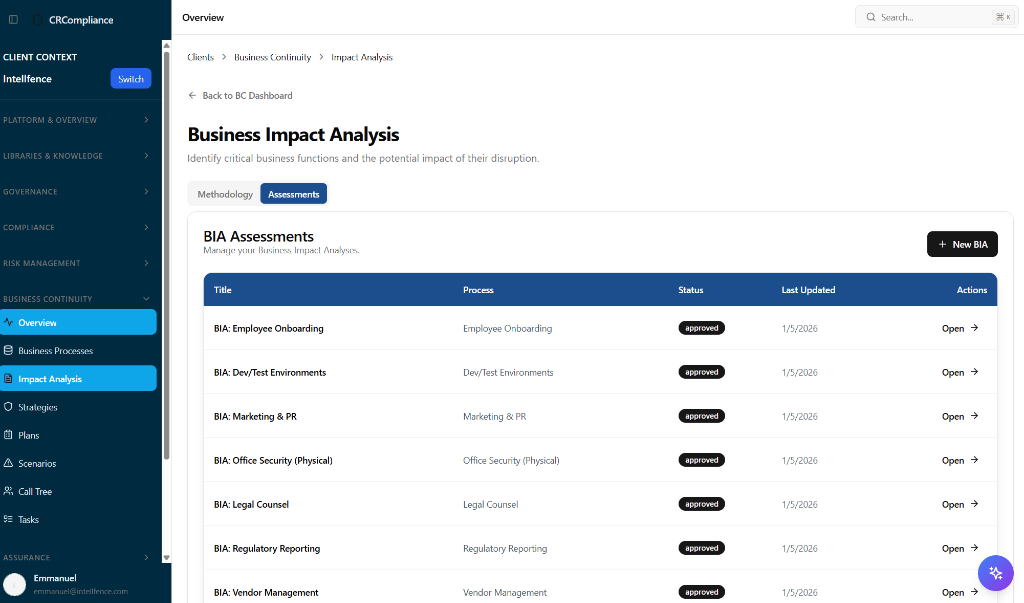
Identify your mission-critical processes and define recovery strategies. Built-in BIA and Disaster Recovery planning modules.